Managing Multiple
Access Points?
Visualize Your WiFi Landscape with inSSIDer!
Have you ever wondered if someone is trying to spoof your network to acquire confidential information? With the advent and rising popularity of public WiFi networks, this event has become all too common. Hackers can easily duplicate a network’s SSID and lead returning clients to automatically associate to the duplicated SSID (this is known as a honeypot attack) without the user realizing they’re not connected to the correct network.
Often the hacker sets up their own laptop as a proxy server for Internet access, allowing the victim to connect to the Internet and transmit data without reason to believe their security has been compromised. The hacker then begins capturing all packet traffic and data passing through, an action otherwise known as a man-in-the-middle attack.
This might lead users to believe public WiFi networks are simply not worth the hassle. But avoiding this whole ordeal is as simple as using the AP aliasing features of MetaGeek software like inSSIDer or Chanalyzer, ensuring the network you connect to is the real Slim Shady™… er, network.
Visualize Your WiFi Landscape with inSSIDer!
The broadcasted SSID here at MetaGeek is “MetaGeek,” naturally. Here is what the MetaGeek network with two APs and four radios looks like without AP Aliasing:
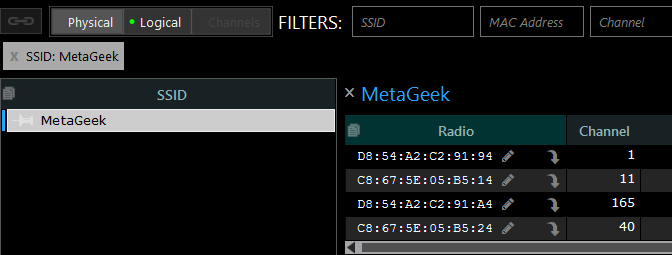
To make sure you know which networks are yours, you can alias them by selecting the first radio in Physical mode and clicking the pencil icon. These are now named “MetaGeek Trusted.”
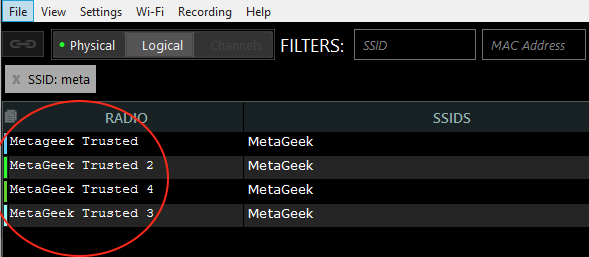
Here is what the final result look like. The four radios here at MetaGeek all have “Trusted” in their alias. (Keep in mind that inSSIDer Office and Chanalyzer can automatically pull aliases from Cisco AP beacons, which is handy for Cisco network admins)
Now, we can check our work by setting up a spoofed network with the MetaGeek SSID using a WiFi Pineapple, similar to what a hacker would try and do. This is how that looks in the Networks Table of Chanalyzer or inSSIDer Plus:
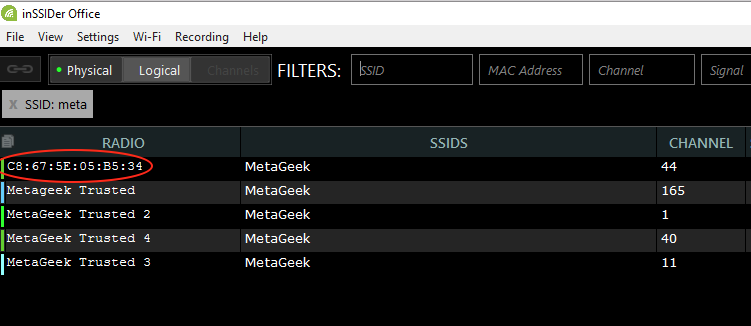
Notice how one radio still contains a MAC address instead of the “trusted” alias? That’s the spoof one– you know that it is an imposter because it has not been aliased. If this were a real attack, you could track down the imposter AP by playing hot/cold with the signal strength level.
Now that you know how to alias your networks in Chanalyzer or inSSIDer Plus, you can easily determine which networks are safe and which networks are imposters, so you can protect yourself and others from man-in-the-middle attacks.
Next Lesson...
Dead Spots and Slow Zones
inSSIDer is the most popular WiFi scanner on Windows. Get started now with inSSIDer!